- Introduction
- Roles of CAs (Root CA / Intermediate CA)
- How Trust Is Ensured by Certificate Authorities
- Hands-on: Building a CA and Issuing Certificates
- Conclusion
Introduction
Ensuring the trustworthiness of your website through certificates is essential for providing secure web services. Websites without verified trust can lead to user loss and increased security risks.
In this article, I explain how to use the OpenSSL command on a Linux server to set up a private CA (Certificate Authority) and an intermediate CA, and issue server certificates. By learning with hands-on practice, you can quickly acquire the skills needed to build secure websites that are ready for real-world use.
Roles of CAs (Root CA / Intermediate CA)
A Certificate Authority (CA) is a trusted third-party organization that ensures secure communication over the Internet. It is especially used to verify that a website is legitimate.
CAs are divided into Root CAs, which occupy the highest level of trust, and Intermediate CAs, which sit between the Root CA and the website. Using Intermediate CAs offers several advantages: it protects the Root CA’s private key to enhance security, and it allows operational flexibility by separating Intermediate CAs for different purposes (e.g., EV certificates, DV certificates, IoT certificates), clarifying management responsibilities and operational rules.
Root CA
- The highest-trust certificate authority
- Delegates trust by signing Intermediate CAs
- Private key is strictly managed, usually kept offline
- Operated by companies such as DigiCert or GlobalSign, as well as non-profit organizations like ISRG (operator of Let’s Encrypt)
Intermediate CA
- Holds a certificate signed by the Root CA
- Issues server/client certificates to websites
- If the Intermediate CA’s private key is compromised, only that specific Intermediate CA is revoked
- Multiple Intermediate CAs can be managed for different purposes (e.g., EV, DV)
How Trust Is Ensured by Certificate Authorities
This diagram illustrates how the trustworthiness of a website is guaranteed using a Root CA and Intermediate CAs.
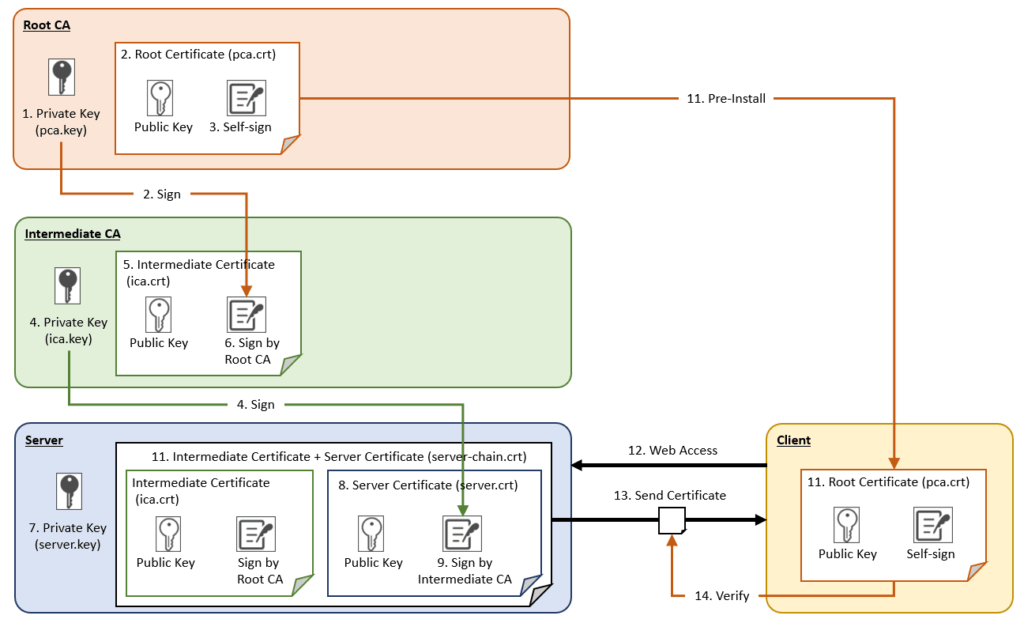
- Create a private key on the Root CA It is critical to ensure this key is never leaked.
- Create the Root Certificate Use the Root CA’s private key to generate the Root Certificate.
- Root CA signs itself
- Create a private key on the Intermediate CA
- Create the Intermediate Certificate Use the Intermediate CA’s private key to generate the Intermediate Certificate.
- Sign the Intermediate Certificate with the Root CA’s private key
- Create a private key on the server
- Create the Server Certificate Use the server’s private key to generate the Server Certificate.
- Sign the Server Certificate with the Intermediate CA’s private key
- Merge and deploy the Intermediate and Server Certificates Commonly deployed on Load Balancers, Apache, nginx, etc.
- Deploy the Root Certificate on the client For widely trusted Root Certificates, this is usually already included in the OS or browser.
- Client sends an access request
- Server sends the Intermediate and Server Certificates
- Client verifies the certificates using the Root Certificate
Hands-on: Building a CA and Issuing Certificates
Learn the practical process of ensuring a website’s trustworthiness by building your own Root CA as a private CA and issuing certificates through a hands-on exercise.
Creating Certificates on the Root CA
First, let’s go through the steps to create certificates on the Root CA.
Create Directories
Set up directories to store keys and certificates:
- /etc/pki/tls/pca/private: Store private keys
- /etc/pki/tls/pca/certs: Store certificates
- /etc/pki/tls/pca/newcerts: Store issued certificates, organized by serial number
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/pca/private
[root@appserver-dev ~]# chmod 700 /etc/pki/tls/pca/private
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/pca/certs
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/pca/newcerts
[root@appserver-dev ~]# ls -ld /etc/pki/tls/pca/private /etc/pki/tls/pca/certs /etc/pki/tls/pca/newcerts
drwxr-xr-x 2 root root 21 Jul 30 12:52 /etc/pki/tls/pca/certs
drwxr-xr-x 2 root root 38 Jul 30 14:36 /etc/pki/tls/pca/newcerts
drwx------ 2 root root 21 Jul 30 12:52 /etc/pki/tls/pca/private
[root@appserver-dev ~]#Create the Configuration File
The series of tasks required to create certificates can be performed using the openssl command. In advance, you should prepare an OpenSSL configuration file to define certificate issuance policies, directories, file paths, and other necessary settings.
Below is a sample openssl.conf file—please edit it to match your environment.
[root@appserver-dev ~]# vi /etc/pki/tls/pca/pca-openssl.conf
[root@appserver-dev ~]# cat /etc/pki/tls/pca/pca-openssl.conf
[ ca ]
default_ca = CA_default
[ CA_default ]
dir = /etc/pki/tls/pca
certs = $dir/certs
crl_dir = $dir/crl
new_certs_dir = $dir/newcerts
database = $dir/index.txt
serial = $dir/serial
RANDFILE = $dir/private/.rand
private_key = $dir/private/pca.key
certificate = $dir/certs/pca.crt
crlnumber = $dir/crlnumber
crl = $dir/crl/pca.crl
crl_extensions = crl_ext
default_crl_days = 30
default_md = sha256
name_opt = ca_default
cert_opt = ca_default
default_days = 3650
preserve = no
policy = policy_strict
[ policy_loose ]
countryName = optional
stateOrProvinceName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits = 4096
distinguished_name = req_distinguished_name
string_mask = utf8only
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name
localityName = Locality Name
0.organizationName = Organization Name
organizationalUnitName = Organizational Unit Name
commonName = Common Name
emailAddress = Email Address
countryName_default = JP
stateOrProvinceName_default = Tokyo
localityName_default = Chiyoda
0.organizationName_default = My Root CA Org
organizationalUnitName_default = Root CA Unit
commonName_default = My Root CA
emailAddress_default = pca@example.com
[ v3_ca ]
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ crl_ext ]
authorityKeyIdentifier=keyid:always
[root@appserver-dev ~]#<Explanation of the Configuration File>
[ca] Section
Specifies which CA settings to use.
- default_ca = CA_default Sets the [CA_default] section as the default.
[CA_default] Section
Specifies the basic directory settings and file names.
- dir Sets the base directory path for the CA. (Change according to your environment.)
- private_key The CA’s private key file (e.g., pca.key).
- certificate The CA’s own certificate file (e.g., pca.crt).
- default_days The validity period (in days) of issued certificates.
[policy_loose] Section
Specifies which fields in the Certificate Signing Request (CSR) are required.
- commonName = supplied Only the CN (Common Name) is required here; all other fields are optional.
[req] Section
Sets default values when creating a CSR.
- default_bits Specifies the default key length.
- distinguished_name Specifies the fields used in the input prompt.
- string_mask Defines character encoding constraints; here, only UTF-8 is allowed.
[req_distinguished_name] Section
Sets the fields and default values for CSR input. Predefining values helps prevent input errors when creating multiple certificates.
[v3_ca] Section
Defines extensions for Root or Intermediate Certificates. Usually not needed for standard server certificates.
- basicConstraints = critical, CA:true → Indicates that this certificate is a CA.
[crl_ext] Section
Specifies extensions for the CRL (Certificate Revocation List).
- authorityKeyIdentifier = keyid:always → Indicates which CA issued this CRL.
Prepare Certificate Issuance Management Files
Prepare the management files required for issuing certificates as a CA.
- index.txt A database file that manages the issuance history of certificates. This file is required when using OpenSSL’s CA functionality, and it records a list of all issued certificates.
[root@appserver-dev ~]# touch /etc/pki/tls/pca/index.txt- serial A file that manages the serial numbers assigned to certificates. The initial value is set to 1000.
[root@appserver-dev ~]# echo 1000 > /etc/pki/tls/pca/serialCreating the Root CA Private Key
I create the private key to be used by the Root CA. Since the private key is highly sensitive, it is encrypted using AES-256 and protected with a passphrase.
[root@appserver-dev ~]# openssl genrsa -aes256 -out /etc/pki/tls/pca/private/pca.key 4096
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
[root@appserver-dev ~]#Command Explanation:
- openssl genrsa
A subcommand used to generate an RSA private key. - -aes256
Encrypts the private key using AES-256-CBC and protects it with a passphrase. This ensures that even if the private key file is leaked, it cannot be used without the passphrase. - -out /etc/pki/tls/pca/private/pca.key
Specifies the location where the generated private key will be saved. - 4096
Specifies the key length in bits. A 4096-bit key is very strong and suitable for a Root CA that will be used over a long period.
Creating the Root CA Certificate (Self-Signed Certificate)
I create the certificate that serves as the trust anchor for the Root CA. Since a Root CA cannot rely on an external certificate authority, it issues the certificate by signing it itself (self-signed).
[root@appserver-dev ~]# openssl req -config /etc/pki/tls/pca/pca-openssl.conf \
-key /etc/pki/tls/pca/private/pca.key \
-new -x509 -days 3650 -sha256 -extensions v3_ca \
-out /etc/pki/tls/pca/certs/pca.crt
Enter pass phrase for /etc/pki/tls/pca/private/pca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [JP]:
State or Province Name [Tokyo]:
Locality Name [Chiyoda]:
Organization Name [My Root CA Org]:
Organizational Unit Name [Root CA Unit]:
Common Name [My Root CA]:
Email Address [pca@example.com]:
[root@appserver-dev ~]#Command Explanation:
- openssl req A subcommand used to create a Certificate Signing Request (CSR) or a certificate.
- config /etc/pki/tls/pca/pca-openssl.conf Specifies the configuration file containing various information to include in the certificate (such as organization name and common name). This automatically sets default values for interactive prompts.
- key /etc/pki/tls/pca/private/pca.key Specifies the Root CA private key to be used for signing.
- new -x509 Creates a new certificate and issues it as a self-signed certificate instead of a CSR.
- days 3650 Sets the certificate validity period to 3,650 days (approximately 10 years).
- sha256 Uses SHA-256 as the signing algorithm.
- extensions v3_ca Applies CA-specific extensions to indicate that this certificate is a CA.
- out /etc/pki/tls/pca/certs/pca.crt Specifies the output file for the Root CA certificate.
Creating Certificates for the Intermediate CA
Next, let’s proceed with the certificate creation process for the Intermediate CA. The basic workflow is almost the same as that for the Root CA, but here we will focus on the differences.
Directory Creation:
- /etc/pki/tls/ica/csr: Stores the CSRs.
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/ica/private
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/ica/certs
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/ica/newcerts
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/ica/csrCreating the Configuration File
Create the configuration file for the Intermediate CA.
[root@appserver-dev ~]# vi /etc/pki/tls/ica/ica-openssl.conf
[root@appserver-dev ~]# cat /etc/pki/tls/ica/ica-openssl.conf
[ ca ]
default_ca = CA_default
[ CA_default ]
dir = /etc/pki/tls/ica
certs = $dir/certs
crl_dir = $dir/crl
new_certs_dir = $dir/newcerts
database = $dir/index.txt
serial = $dir/serial
crlnumber = $dir/crlnumber
RANDFILE = $dir/private/.rand
private_key = $dir/private/ica.key
certificate = $dir/certs/ica.crt
crl = $dir/crl/ica.crl
crl_extensions = crl_ext
default_crl_days = 30
default_md = sha256
name_opt = ca_default
cert_opt = ca_default
default_days = 1825
preserve = no
policy = policy_loose
[ policy_loose ]
countryName = optional
stateOrProvinceName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits = 4096
distinguished_name = req_distinguished_name
string_mask = utf8only
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name
localityName = Locality Name
0.organizationName = Organization Name
organizationalUnitName = Organizational Unit Name
commonName = Common Name
emailAddress = Email Address
countryName_default = JP
stateOrProvinceName_default = Tokyo
localityName_default = Chiyoda
0.organizationName_default = My Intermediate CA Org
organizationalUnitName_default = Intermediate CA Unit
commonName_default = My Intermediate CA
emailAddress_default = intermediateca@example.com
[ v3_ca ]
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer
basicConstraints = critical, CA:true, pathlen:0
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ server_cert ]
basicConstraints = CA:FALSE
nsCertType = server
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = debug.quiz.eeengineer.com
[ crl_ext ]
authorityKeyIdentifier=keyid:alwaysExplanation of Additional Items in the Root CA Configuration File
[server_cert] Section
Extensions applied to certificates used for TLS on servers (e.g., HTTPS):
- basicConstraints = CA:FALSE Indicates that this is a server certificate and restricts its use as a CA.
- nsCertType = server Specifies that the certificate is intended for server use.
- keyUsage = critical, digitalSignature, keyEncipherment Allows only the key usages required for a server certificate: signing and key exchange.
- extendedKeyUsage = serverAuth Clearly indicates that the certificate is for server authentication only.
- subjectAltName = @alt_names A crucial setting for server certificates, used to define the certificate’s host name (FQDN).
[alt_names] Section
Specifies the domain names (FQDNs) for which the server certificate is valid. Browsers and clients always check the subjectAltName; if it does not match, a certificate error occurs.
- DNS.1 = debug.quiz.eeengineer.com
In this example, only debug.quiz.eeengineer.com is valid.
Creating Certificate Management Files
As with the Root CA, create the index.txt and serial files to manage issued certificates.
[root@appserver-dev ~]# touch /etc/pki/tls/ica/index.txt
[root@appserver-dev ~]# echo 1000 > /etc/pki/tls/ica/serial- crlnumber
This file is used to manage the version number assigned to the CRL. It is initialized to 1000.
[root@appserver-dev ~]# echo 1000 > /etc/pki/tls/ica/crlnumberCreating the Intermediate CA Private Key
The command to create the private key is the same as the one used for the Root CA. Only the file name and path need to be changed.
[root@appserver-dev ~]# openssl genrsa -aes256 -out /etc/pki/tls/ica/private/ica.key 4096
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
[root@appserver-dev ~]#Creating the CSR
Generate a CSR to request certificate issuance from the Root CA.
[root@appserver-dev ~]# openssl req -config /etc/pki/tls/ica/ica-openssl.conf \
-new -sha256 -key /etc/pki/tls/ica/private/ica.key \
-out /etc/pki/tls/ica/csr/ica.csr
Enter pass phrase for /etc/pki/tls/ica/private/ica.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [JP]:
State or Province Name [Tokyo]:
Locality Name [Chiyoda]:
Organization Name [My Intermediate CA Org]:
Organizational Unit Name [Intermediate CA Unit]:
Common Name [My Intermediate CA]:
Email Address [intermediateca@example.com]:
[root@appserver-dev ~]#Command Explanation:
- openssl req
A command used to generate and process Certificate Signing Requests (CSRs). - -config /etc/pki/tls/ica/ica-openssl.conf
Specifies the configuration file to use. Here, it loads the configuration customized for the Intermediate CA. - -new
Indicates that a new CSR is being created. - -sha256
Specifies SHA-256 as the hashing algorithm. SHA-256 is stronger than SHA-1 and is recommended for improved security. - -key /etc/pki/tls/ica/private/ica.key
Specifies the private key file used to create the CSR. The corresponding public key information is included in the CSR. - -out /etc/pki/tls/ica/csr/ica.csr
Specifies the output file for the generated CSR.
Signing and Certificate Issuance by the Root CA
The Root CA signs the CSR and issues the certificate.
[root@appserver-dev ~]# openssl ca -config /etc/pki/tls/pca/pca-openssl.conf \
-policy policy_loose \
-extensions v3_ca -days 3650 -notext -md sha256 \
-in /etc/pki/tls/ica/csr/ica.csr \
-out /etc/pki/tls/ica/certs/ica.crt
Using configuration from /etc/pki/tls/pca/pca-openssl.conf
Enter pass phrase for /etc/pki/tls/pca/private/pca.key:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4097 (0x1001)
Validity
Not Before: Jul 30 05:36:03 2025 GMT
Not After : Jul 29 05:36:03 2030 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
organizationName = My Intermediate CA Org
organizationalUnitName = Intermediate CA Unit
commonName = My Intermediate CA
emailAddress = intermediateca@example.com
X509v3 extensions:
X509v3 Subject Key Identifier:
16:AF:A5:CE:08:5C:64:02:98:2C:71:21:13:CD:5B:B2:72:CB:00:98
X509v3 Authority Key Identifier:
DB:11:C4:ED:3E:C2:EE:C4:F7:9D:B3:F8:ED:4A:D4:98:E1:BA:ED:58
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
Certificate is to be certified until Jul 29 05:36:03 2030 GMT (1825 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
[root@appserver-dev ~]#Command Explanation:
- openssl ca A command used to sign Certificate Signing Requests (CSRs) and issue certificates as a CA.
- config /etc/pki/tls/pca/pca-openssl.conf Specifies the OpenSSL configuration file for the Root CA.
- policy policy_loose Specifies the policy for verifying the CSR content. Here, policy_loose is used to relax the required fields.
- extensions v3_ca Specifies the extensions to include in the issued certificate. v3_ca adds CA-specific extensions (e.g., basicConstraints=CA:true).
- days 3650 Sets the validity period of the issued certificate in days. Here, it is set to 3,650 days (approximately 10 years).
- notext Omits textual details from the certificate output to reduce file size.
- md sha256 Specifies the hash function for signing the certificate. SHA-256 is used to enhance security.
- in /etc/pki/tls/ica/csr/ica.csr Specifies the CSR file to be signed.
- out /etc/pki/tls/ica/certs/ica.crt Specifies the output file for the issued certificate.
Creating the Server Certificate
Finally, let’s proceed with creating the server certificate.
Directory Creation
As before, create the necessary directories.
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/server/private
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/server/csr
[root@appserver-dev ~]# mkdir -p /etc/pki/tls/server/certsCreating the Configuration File
Create the configuration file for generating the server certificate.
[root@appserver-dev certs]# vi /etc/pki/tls/server/server-openssl.conf
[root@appserver-dev certs]# cat /etc/pki/tls/server/server-openssl.conf
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
req_extensions = v3_req
prompt = no
[ req_distinguished_name ]
C = JP
ST = Tokyo
L = Adachi
O = eeengineer Org
OU = Certificate Unit
CN = debug.quiz.eeengineer.com
[ v3_req ]
subjectAltName = @alt_names
keyUsage = digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
[ alt_names ]
DNS.1 = debug.quiz.eeengineer.com
[root@appserver-dev certs]#
Explanation of the Configuration File
[req] Section
Sets the basic configuration for creating a Certificate Signing Request (CSR):
- default_bits = 2048 Sets the key length to 2048 bits.
- distinguished_name = req_distinguished_name Loads the Distinguished Name (DN) fields to include in the CSR from the req_distinguished_name section.
- req_extensions = v3_req Loads the extensions to include in the CSR from the v3_req section.
- prompt = no Skips interactive prompts and automatically uses the values specified in the configuration file.
[req_distinguished_name] Section
Specifies the identification information (DN) to include in the CSR.
[v3_req] Section
Specifies the extensions to include in the CSR:
- subjectAltName = @alt_names
Specifies the Subject Alternative Name (SAN), loading domain names from the alt_names section. SAN is required for hostname verification in TLS certificates. - keyUsage = digitalSignature, keyEncipherment
Restricts the key usage. - digitalSignature
Used for digital signatures. - keyEncipherment
Used for key exchange (required for TLS key exchange). - extendedKeyUsage = serverAuth
Specifies that the certificate is intended for server authentication.
Creating the Server Private Key
Generate the private key to be used by the server.
[root@appserver-dev ~]# openssl genrsa -out /etc/pki/tls/server/private/server.key 2048Creating the CSR
Generate the CSR by specifying the configuration file and the private key.
[root@appserver-dev ~]# openssl req -new -key /etc/pki/tls/server/private/server.key -out /etc/pki/tls/server/csr/server.csr -config /etc/pki/tls/server/server-openssl.confSigning and Certificate Issuance by the Intermediate CA
The Intermediate CA signs the CSR and issues the certificate.
[root@appserver-dev ~]# openssl ca -config /etc/pki/tls/ica/ica-openssl.conf \
-extensions server_cert -days 3650 -notext -md sha256 \
-in /etc/pki/tls/server/csr/server.csr \
-out /etc/pki/tls/server/certs/server.crt
Using configuration from /etc/pki/tls/ica/ica-openssl.conf
Enter pass phrase for /etc/pki/tls/ica/private/ica.key:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4096 (0x1000)
Validity
Not Before: Jul 30 05:40:53 2025 GMT
Not After : Nov 2 05:40:53 2027 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
organizationName = eeengineer Org
organizationalUnitName = Certificate Unit
commonName = debug.quiz.eeengineer.com
emailAddress = eeengineer@gmail.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Cert Type:
SSL Server
Netscape Comment:
OpenSSL Generated Server Certificate
X509v3 Subject Key Identifier:
B2:9B:83:15:DF:51:2D:2D:EC:91:4F:96:DB:89:46:5C:42:37:41:A8
X509v3 Authority Key Identifier:
16:AF:A5:CE:08:5C:64:02:98:2C:71:21:13:CD:5B:B2:72:CB:00:98
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
Certificate is to be certified until Nov 2 05:40:53 2027 GMT (825 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
[root@appserver-dev ~]#Creating the Certificate Chain File
Use the cat command to combine the Intermediate Certificate and the Server Certificate to create a chain certificate (server-chain.crt). This chain certificate is required when deploying to web servers such as Apache or Nginx. Be careful to list the certificates in the correct order: first the Intermediate Certificate, followed by the Server Certificate.
[root@appserver-dev ~]# cat /etc/pki/tls/server/certs/server.crt \
/etc/pki/tls/ica/certs/ica.crt > /etc/pki/tls/server/certs/server-chain.crt
[root@appserver-dev ~]#
[root@appserver-dev ~]# cat /etc/pki/tls/server/certs/server-chain.crt
-----BEGIN CERTIFICATE-----
MIIFeTCCA2GgAwIBAgICEAEwDQYJKoZIhvcNAQELBQAwgaUxCzAJBgNVBAYTAkpQ
MQ4wDAYDVQQIDAVUb2t5bzEfMB0GA1UECgwWTXkgSW50ZXJtZWRpYXRlIENBIE9y
~~~~
V9zFUV1d3iJhGD9mNY7nckDo3qrbENmSiaZ/v9yVB8+jRU+kncr2Wk1e45BGpY+q
npOh/Bu9A3bRv5DAyNO4ZmgbW1KitIBALFWYnjKof7/Db0ZkBtwvGfp0WUKMOg8b
SgjBhHRHPbhtP5P7XQ==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIGGjCCBAKgAwIBAgICEAEwDQYJKoZIhvcNAQELBQAwgZQxCzAJBgNVBAYTAkpQ
MQ4wDAYDVQQIDAVUb2t5bzEQMA4GA1UEBwwHQ2hpeW9kYTEXMBUGA1UECgwOTXkg
~~~~
uQ74+ir76BLXaWnzmbadJF4S1oVmhOZTWdYe3Vjiw16fsWVWYb2iddkjYT+8FCsI
odeNEZZY2Ol59N20yzo63gzytOZ9GU8mDvO6EzuF2kWKDNFDD6/5MBEbjK5SUBQE
5sha226CBEB2yW68GRxIuvM9gTyKP4T3zdrjBAV6
-----END CERTIFICATE-----
[root@appserver-dev ~]#Conclusion
This concludes the explanation of building a private CA and intermediate CA, and the procedure for issuing server certificates. A separate article explains how to deploy the issued certificates to a web server and verify the server authentication process. Reading it alongside this guide will help deepen your understanding. Be sure to check it out.



コメント